
How 5G Supports Lawful Interception
The idea of a government being able to intercept its citizens’ communications is that of an Orwellian novel. In reality, to a degree, communication interception is a possibility. In contrast to 1984, for government bodies to intercept data, there is a strict set of guidelines and procedures put in place. In the UK, the penalty for unlawful interception is up to two years imprisonment or an uncapped fine. Before LI (Lawful Intercept) can occur, a warrant outlining the purpose of the interception, what data is going to be obtained, and the dates which it will be obtained between must be provided and approved by a legal body. Figure 1 provides a list of warrant types that are relevant to LI in 5G:
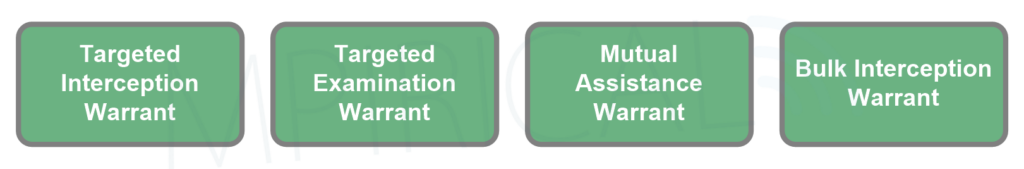
- Targeted Interception Warrant – this warrant targets specific individuals and a narrow range of communications, typically issued for criminal investigations or national security.
- Targeted Examination Warrant – used to analyse and extract information from previously obtained data, the warrant specifies individuals or entities to limit the scope of the examination.
- Mutual Assistance Warrant – a mutual assistance warrant facilitates cooperation between jurisdictions and is commonly used in international criminal investigations, such as terrorism, drug trafficking, cybercrime, and money laundering. It allows authorities to request evidence or assistance from other countries, aligning with MLAT (Mutual Legal Assistance Treaties).
- Bulk Interception Warrant – bulk interception warrants enable the interception of large volumes of communications data without naming or describing specific targets, serving as a strategic intelligence tool, unlike targeted interception warrants, which are investigative and are often used after bulk interception results.
Data collected under these warrants follows strict handling and storage protocols to protect individuals’ privacy. The balance between effective law enforcement and privacy rights is debated, requiring safeguards like judicial authorisation, time limits, and scope restrictions to prevent abuse.
What is the 5G Lawful Intercept Process?
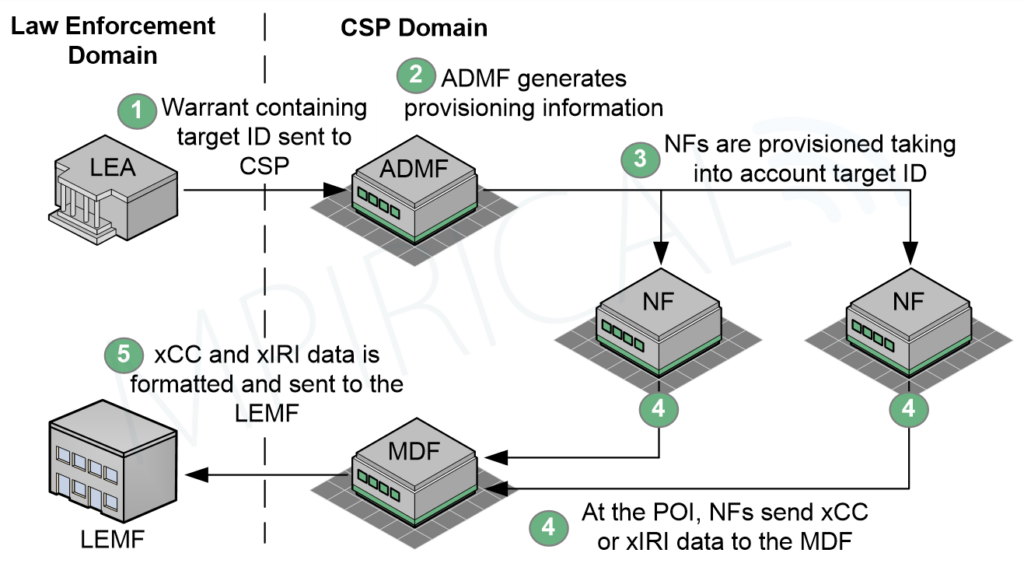
So, we’ve identified the types of warrants which can be utilised; the next stage is to understand how they initiate the LI process in 5G. Figure 2 outlines the end-to-end process of LI in 5G, highlighting the essential functions.
To begin with, the LEA (Law Enforcement Agency) sends the warrant to one (or many) CSP (Communication Service Providers), specifically to the ADMF (Administration Function). The ADMF handles many different warrants at a time and is the control function for the LI process within the 5G Core. At the ADMF, provisioning information is generated, which is used to (believe it or not) provision other network functions in the 5G Core. NFs (Network Functions) will be provided with what specific data they are required to capture; we will explore these different data types in the next section. Additionally, NFs are told the address of the MDF (Mediation and Delivery Function), which will collate all of this data and package it to be ready for delivery to the LEMF (Law Enforcement Monitoring Facility). The LEMF is the endpoint of the LI process and handles all received data in a structured manner:
What Type of Data Can Be Obtained?
Now, let’s talk about the different data types that can be obtained. There are two flavours of intercept data: IRI (Intercept Related Information) and CC (Content of Communication)
IRI Data contains a broad range of metadata that can provide insight into communication patterns and provide context. Examples of this type of information include CDRs (Call Detail Records), session initiation and termination times, location-based information, and IP (Internet Protocol) addresses.
CC Data encompasses communication content, including voice recordings, internet browsing data, social media interactions, and file transfers. This provides the actual substance of communication that can support investigations. It’s important to remember that nowadays, the majority of our CC data is encrypted, especially when using OTT (Over-The-Top) applications such as WhatsApp or the Internet. Therefore, this data type is often not as helpful as IRI Data.
Conclusion
In conclusion, while lawful interception allows governments to access and analyse communication data under specific warrants, strict legal frameworks and procedures exist to protect citizens’ privacy. Various warrant types, such as targeted, bulk interception, and mutual assistance warrants, serve distinct roles in criminal investigations and national security. The 5G Lawful Intercept process involves precise coordination among network functions and law enforcement agencies to ensure specific data is captured, processed, and analysed effectively while adhering to strict procedures. Additionally, the distinction between IRI and CC highlights the importance of metadata in investigations, particularly as encryption continues to limit the accessibility of direct communication content.
If you would like to learn more about how 5G and other cellular technologies support lawful interception, check out our course on Lawful Interception, which can be viewed on-demand or presented live by our expert instructors.
