
Reducing Risk through Network Analytics
Defined by the ITU (International Telecommunication Union) as one of the three usage scenarios for 5G, MMTC (Massive Machine Type Communications) or MIoT (Massive Internet of Things) is likely to be the catalyst for the transition of mobile networks away from primarily human centric communication.
In fact a recent report by Ericsson forecast that by 2026, 70.3% (26.9 Billion) of all connected devices globally will be supporting IoT type traffic whereas mobile phones are only expected to represent 21.6% (8.3 Billion).
Identifying the Risk
So, what will be the impact of this switch in device and traffic type? Well, clearly there will be considerable impact upon network utilization, systems optimization (both in the RAN (Radio Access Network) and Core) not to mention how these services will actually be monetized. However, rather than talking about the wide range of services, applications and verticals that are likely to drive this growing ecosystem, I wanted to look specifically at some of the security issues and associated risks and in so doing, review how these may be addressed through network analytics.
Clearly with billions of connected devices, be that smart meters, parking sensors, street lights or asset trackers etc, there is, please ignore the pun, “massive” opportunities for these devices to be misused or even hijacked. In fact we should also consider the impact of poorly designed hardware and software which has already accounted for numerous network issues and signalling storms. Therefore, it becomes imperative that mobile service providers are able to protect their networks from these attacks by using analytics and machine learning to detect, predict and evaluate the risk before actioning the appropriate countermeasure.
Introducing the NWDAF
Introduced in the Release 15 3GPP specifications, the NWDAF (Network Data Analytics Function) forms part of the 5G Core network and is responsible for collecting data and providing analytical services to other functions both within and outside the mobile network. As such, it will communicate with the AMF (Access and Mobility Management Function), SMF (Session Management Function), and PCF (Policy Control Function) within the network and potentially through the NEF (Network Exposure Function) in order to link with other third party application functions.
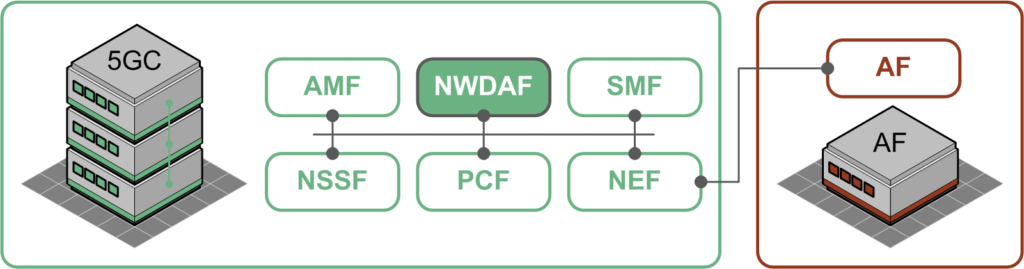
In so doing, the NWDAF will provide support regarding the analysis and prediction of network slice load levels, service experience, network performance etc. and, with regards to reducing risk within the MMTC realm, it will analyse device mobility, expected and abnormal behaviour patterns.
Identifying Misbehaving Devices
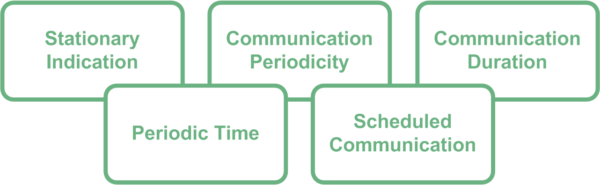
Therefore when a mobile service provider wishes to identify misbehaving devices, they will request the NWDAF supervises either a specific device or more likely, group of devices. As such, the NWDAF will perform data analysis on said devices by comparing their runtime data with expected behaviour. Interestingly, the expected behaviour could be subscription based, such as conformance to a pre agreed SLA (Service Level Agreement), provided directly from third party application servers, or even learned by the NWDAF itself via the collection of historical or training data. Such behavioural information could include:
- Stationary Indication – should the device remain stationary or be permitted to move e.g. smart meter or e-scooter.
- Communication Periodicity – can the device initiate communication or does it need to be triggered.
- Communication Duration – how long will the device be in communication with the network e.g. 5 minutes.
- Periodic Time – how often will the device communicate with the network e.g. once every 24 hours.
- Scheduled Communication – at what time / day of the week will the device be available to communicate e.g. Tuesday at 02:00am.
Therefore, in order for the NWDAF to collect device runtime data, such as the location of a specific device or group of devices, it will need to set up monitoring events with other functions within the 5G Core network. For example, the AMF will be able to provide the location of a device(s) and the SMF will be aware of a change in data flow.
Solving the Risk of Misbehaving Devices
Once the NWDAF conducts its analysis on the runtime data and detects serious misbehaviour e.g. wrong location, abnormal traffic pattern etc. it will then determine whether to notify or alert a specific function within the network or, an external application via the NEF. This will be dependent upon whether these network functions have subscribed to a Risk Report which would have taken place during the device registration procedure i.e. when it powers on.
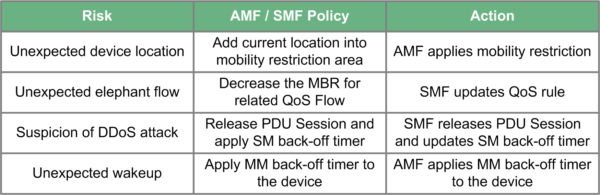
Upon receiving a Risk Report, the network function can then apply a pre-defined policy but clearly, these will be configurable to satisfy the particular requirement / situation. Figure 3 illustrates some example high level policies and actions.
Clearly the NWDAF is not restricted to purely “risk management” roles but instead can be used to provide in depth analytics to further enhance and optimize next generation networks i.e. service experience, QoS sustainability, network performance in areas of interest etc. However, in can also be used to identify misbehaving devices, evaluate the risks, and take the necessary action to protect the network from both intentional and unintentional threats.
