Navigating Cellular – The Evolution of Vulnerabilities from 3G to 5G
In the ever-evolving landscape of telecommunications, the transition from 3G to 5G has not only promised faster speeds, high reliability, and lower latency. It has also introduced new layers of complexity and, consequently, vulnerabilities. As we delve into this progression, it’s crucial to understand the inherent risks associated with each generation of cellular technology and the approaches that can be taken to mitigate vulnerabilities or reduce their impact.
3G Vulnerabilities
As we journey back to the era of 3G, a technological leap that brought mobile data services to the masses, it’s essential to shed light on the vulnerabilities that impacted this groundbreaking technology. 3G networks, while revolutionary, were not immune to security challenges. Eavesdropping and interception exposed user data to prying eyes, while SMS (Short Messaging Service) introduced deceptive practices through manipulating messages. Network congestion attacks posed threats to service availability, prompting the need for resilient network management.
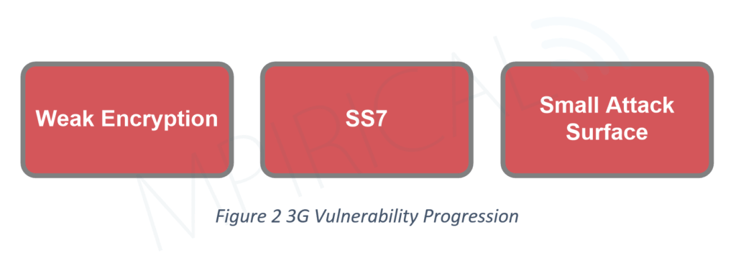
Inadequate encryption algorithms such as A5/1 (introduced within 2G) was used to protect the confidentiality of user data in transit. Even at the time of deployment A5/1 was considered weak. Therefore, it is vulnerable to the aforementioned eavesdropping and interception attacks.
SS7 (Signalling System 7) is a set of protocols used in 3G cellular networks to control the setup, management, and tear-down of phone calls and text messages. It plays a crucial role in global telecommunications but has several vulnerabilities. Attackers can exploit SS7 to intercept SMS messages, track users, impersonate users, manipulate billing, and bypass authentication.
In comparison to its successors, 3G has a small attack surface. This is because of factors such as fewer connected devices, simpler protocols, limited internet usage, and its emphasis on voice and text.
The Transition to 4G: Enhancing Security and Additional Vulnerabilities
As technology advanced to 4G, so did the security protocols utilised. With the implementation of LTE (Long-Term Evolution), communication became more secure through encryption and mutual authentication. While 4G networks were not without vulnerabilities, the enhancements significantly raised the bar for attackers.
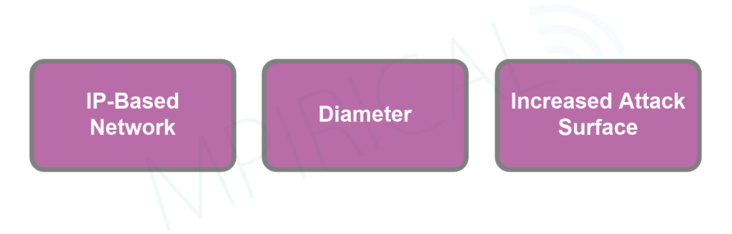
Unlike 3G networks, 4G networks implement IP (Internet Protocol) making them susceptible to IP-related vulnerabilities. These already existing vulnerabilities can be exploited by malicious actors to disrupt services, steal sensitive information, or gain unauthorized access to critical network resources.
Diameter is a protocol used in cellular networks for tasks such as AAA (Authentication, Authorisation, and Accounting). Like any network protocol, Diameter has its own set of vulnerabilities and security concerns. There is the potential to disclose sensitive user information or allow a denial of service.
With the introduction of more connected devices, such as IoT and the utilisation of IP-based networks, the attack surface of cellular networks has vastly increase in comparison to 3G due to the number of connected devices and critical components. 4G networks still have a heavy reliance on 3G networks for calls and SMS. This means that 4G has also adopted vulnerabilities that exist within 3G networks.
5G Unleashed: Speed, Low Latency, High Reliability, and New Vulnerabilities
The deployment of 5G brings promises of unprecedented speed, ultra-low latency, and high reliability, setting the stage for the era of CIoT (Cellular Internet of Things) and MMTC (Massive Machine Type Communications). However, this transition unveiled a new set of vulnerabilities. The expanded attack surface, thanks to the increased number of connected devices, creates more entry points for malicious actors.

One notable vulnerability is the reliance on SDN (Software Defined Networks) and NFV (Network Function Virtualisation). While these technologies enhance the flexibility and scalability of 5G networks, they also introduce additional points of attacks. The distributed nature of 5G networks also poses challenges, making it imperative to secure not only the 5G core but also the various edge devices.
Distributed Edge Computing, a cornerstone of 5G architecture, distributes computing resources closer to the user, increasing reliability, reducing latency, and minimising load on the 5G core. However, this shift brings forth security challenges. The decentralised nature of edge computing demands robust security measures at each node.
Given the critical infrastructure 5G supports, it is an attractive target for state-sponsored cyber-attacks. These attacks can be highly sophisticated and well-funded.
Securing Cellular Networks
Mitigating vulnerabilities involves a multifaceted approach aimed at fortifying the cellular landscape against potential threats. Regular security audits and vulnerabilities assessments provide a proactive means of identifying and addressing weaknesses. Lessons from 3G-5G vulnerabilities have contributed to the adoption of a zero-trust architecture in network security. This approach assumes no implicit trust and requires verification from anyone trying to access resources in the network.
Implementing strong access controls, encryption protocols, and maintaining up-to-date software through regular patches helps to create a defence in depth approach. Network segmentation confines potential breaches limiting the impact of an intrusion. Intrusion detection systems offer real-time monitoring and response, while continuous employee training can be used to enhance the human aspect of mobile service providers.
A well-defined incident response plan ensures swift and effective action in the event of a security breach. Collaborative information sharing and a security-by-design mindset can further increase the resilience of cellular networks. The key lies in a comprehensive strategy that integrates, technology, personnel, and processes to create a resilient and adaptive security posture.
Conclusion
The journey from 3G to 5G represents more than just a technological evolution – it’s a continuous battle to stay ahead of emerging vulnerabilities. As we embrace the benefits presented by 5G, we must also remain vigilant in creating resilient networks to minimise risks and threats. The collaboration between mobile service providers, vendors, standards bodies, governments, and cybersecurity experts becomes paramount in creating a resilient and secure foundation for the future of telecommunications.
For more information on this topic, check out our latest course “Introduction to Cellular Cybersecurity”.
