
5G Anonymity and the SUCI
Across all generations of cellular technology, the notion of a temporary identity has been used to protect the anonymity of the end user. The idea behind this is that the IMSI (International Mobile Subscriber Identity) that is used to uniquely identify a subscription is sensitive information; it will not change unless the SIM is replaced or an eSIM is overwritten.
The problem is that pretty much every time the device has an interaction with the network, it will be required to identify itself. If only the IMSI was used during these interactions and if an attacker was able to gain knowledge of a target’s IMSI, they could potentially track the movement of that subscriber. Consequently, devices are allocated a temporary ID which they will routinely use when interacting with the network, instead of the IMSI. A huge disclaimer at this point will remind readers that the notion of the temporary ID works if that temporary ID is administered correctly; meaning, the mobile service provider must ensure it’s changed on a regular basis!
When you look into the detail, you might think that this kind of attack just isn’t feasible because all of the device to core network traffic tends to be encrypted. To a degree this is true but not completely; there will be times, particularly during network attach/registration, that the IMSI is indeed sent in the clear, with no encryption involved, regardless of whether the device has been allocated a temporary ID.
To explain further, before you can activate signalling security, the network must first identify the subscriber to access the correct master key (amongst other activities such as authentication). Normally, the core network will simply map the temporary ID that the device includes in the Attach Request / Registration Request to the actual IMSI. Occasionally though, the network simply cannot resolve the IMSI from the temporary ID; this will happen for example when the device has been away from the network for a long period of time. Other scenarios where the IMSI has to be provided instead of the temporary ID include switching the device on for the very first time and also during roaming. Bear in mind that security establishment happens after identification, which means that any exchange of the IMSI will be in the clear and susceptible to anyone with access to an IMSI Catcher!

I guess the question is, why would 5G continue with the same approach, potentially maintaining a known security vulnerability? The answer is, it doesn’t. In 5G, the notion of the SUCI (Subscription Concealed Identifier) has been introduced to combat the issue. With the SUCI based approach (pronounced Soo-Kee or Soo-She, depending on who you speak to), the IMSI should never be sent in the clear, regardless of the situation.
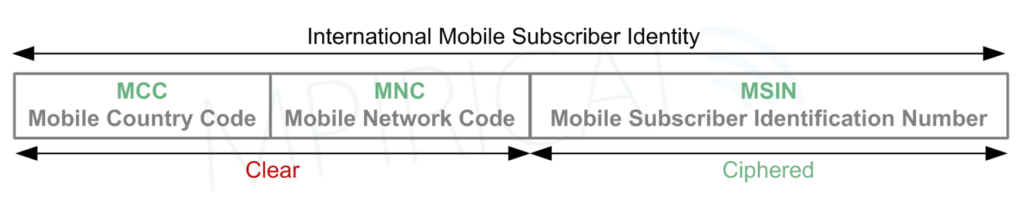
In particular, before sending the IMSI (which is known as the SUPI or Subscription Permanent Identifier in 5G), elements of the IMSI are encrypted. Specifically, the MSIN (Mobile Subscriber Identification Number) portion is encrypted, whereas the MCC (Mobile Country Code) and MNC (Mobile Network Code) remain in the clear for message routing purposes.
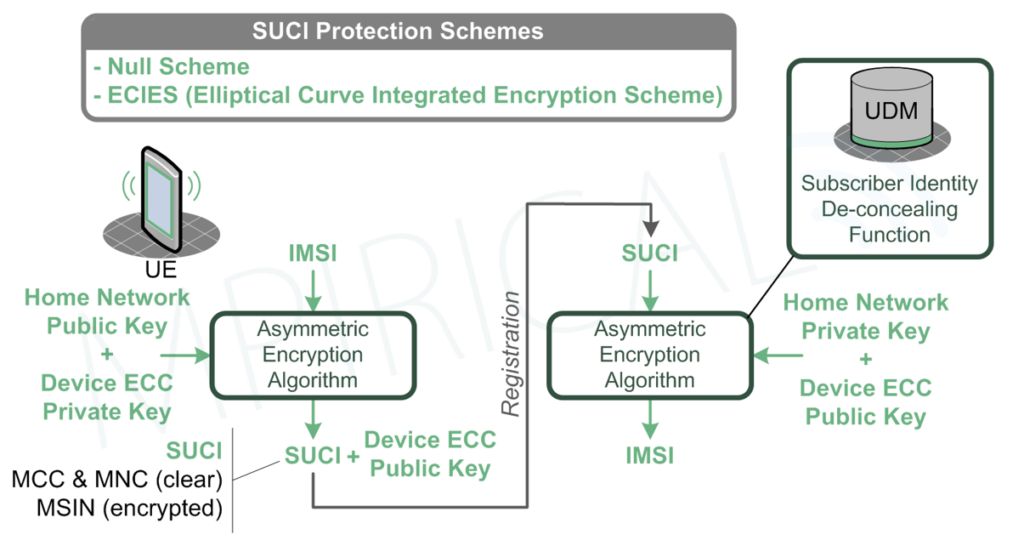
When the SUCI is sent to the network, it’s the responsibility of the UDM (Unified Data Management) to decrypt the SUCI to reveal the true IMSI; an activity that takes place in the rather unimaginatively entitled “Subscriber Identity De-concealing Function”. Of course, to conduct the encryption/decryption, you must have cryptographic keys which in this case, must be asymmetric since we need to distribute keys in the clear. As can be seen in the diagram, the SUCI is actually generated using a combination of a network public key (which must be provisioned on the device by the network), coupled with a device private key (generated by the device as required and based on Elliptical Curve Cryptography). Hence, decryption will be based on the network’s private key, coupled with the device’s ECC public key (embedded in the SUCI – see Figure 5).
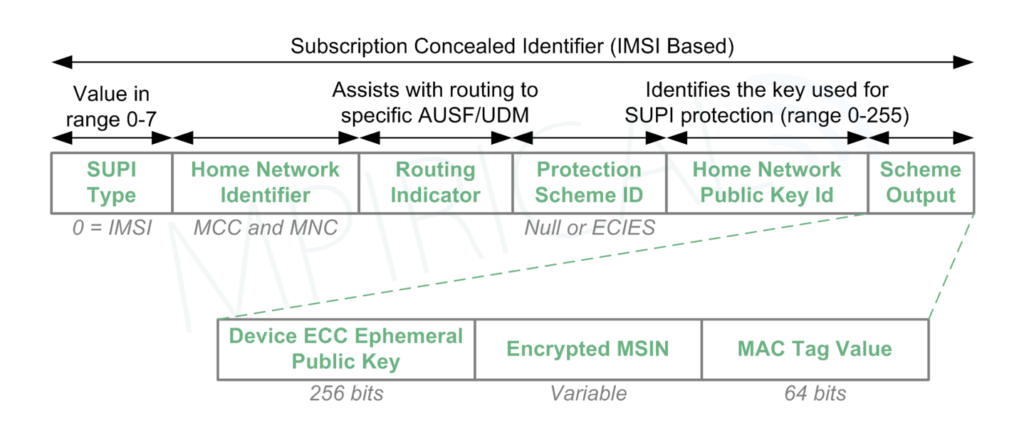
For the last piece of detail, here’s a diagram to show the overall composition of the SUCI (which should be fairly self-explanatory):
Therefore, when the device is required to send the IMSI over an insecure radio link or Wi-Fi connection, the SUPI can help to mitigate the risk posed by IMSI monitoring. There are however a few points to note before we breathe a collective sigh of relief (I mean, who doesn’t lie awake at night worrying about IMSI catchers…?):
- Although the SUCI is always used in signalling, actual encryption of the MSIN element is optional! Therefore instead of using a protection scheme based on ECIES (Elliptical Curve Integrated Encryption Scheme), the service provider could just opt for Null Encryption, meaning the IMSI will essentially be in the clear.
- Use of the SUCI will stop IMSI Catchers from detecting IMSIs in the clear, but won’t help with downgrade attacks since those attacks exploit the device’s cell reselection algorithms.
- Crucially, the SUCI approach will only work if it’s implemented correctly, both at the device and on the network.
- This approach only works with Standalone 5G; all those “5G” networks that are out there based on Non Standalone won’t be using the SUCI.
Final Thoughts…
I’ll admit it, for some people, topics such as this are not the most interesting of areas but for others, this article is barely scratching the surface. Regardless, in an age where our privacy is becoming more and more important (and awareness of lack of privacy becoming more widespread), the 3GPP have almost been obliged to integrate this technique into 5G. We’re now several years on from the first standalone deployments of 5G and it is evident that major operators are definitely on-board with the concept – initially we saw deployments that were using null encryption but these days, it’s very routine for us to see ECIES being used.
Updated: 14th October 2025 by Gavin Mitchell
