
5G Security when Roaming – Part 2
Last month we introduced the topic of security when roaming in 5G and in so doing set out the network architecture and introduced the key functions that are involved. Furthermore, we also focused in on the authentication process which has been amended to now include authentication between the visited network (VPLMN) and the home network (HPLMN) to verify that they do actually have a “live” connection with the subscriber.
This month, we are going to turn our attention to the actual interconnection between the two networks and in so doing, focus on how we can secure both the control and user planes as they span the IPX (IP eXchange).
Securing the Control Plane
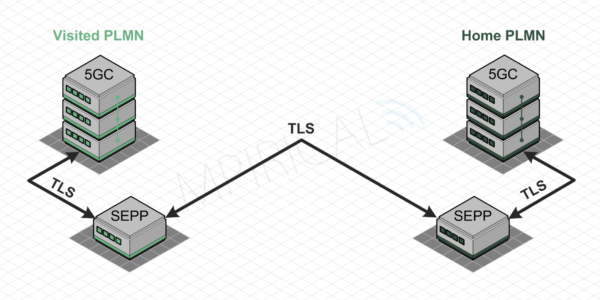
Within the 5GC (5G Core) network, all network functions must support mutually authenticated TLS (Transport Layer Security) and HTTPS (HyperText Transport Protocol Secure) and thus use client and server certificates to protect the control plane signalling. This may also be used in a roaming environment to secure the connection not only between the network functions and the SEPP (Security Edge Protection Proxy) but also between SEPPs (N32) in the visited and home PLMNs. However if there are any IPX entities between the SEPPs, PRINS (Protocol for N32 Interconnect Security) is used instead of TLS. This concept is illustrated in Figure 1 and Figure 2.
Transport Layer Security
Using TLS between the SEPPs provides high degrees of security with all signalling passing between the visited and home networks being encrypted on an end-to-end basis. However, this solution is complicated to manage with an increasing number of “n×n” roaming connections. Furthermore, this architecture completely excludes the role of roaming VAS (Value Added Service) service providers and degrades the role of IPX service providers to being simply an IP routing service. As such, this solution only really works for the top roaming relationships e.g. service providers within the same group rather than between all service providers within the overall mobile ecosystem.
Protocol for N32 Interconnect Security
PRINS adds application layer security whereby part of the signalling may be sent in the clear such that VAS and IPX service providers can inspect and / or modify the signalling whilst it is in transit. This is rather complicated and calls upon the “receiving” network to verify these modifications which may have been carried out by the intermediate service providers. Therefore, the SEPPs will use JWE (JSON Web Encryption) to protect the messages they send across N32 whereas the IPX service providers will use JWS (JSON Web Signatures) to sign the modifications they made during transit across the IPX.
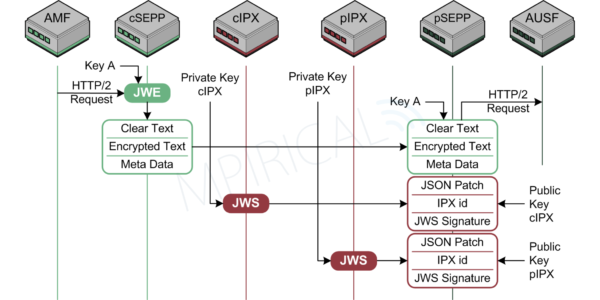
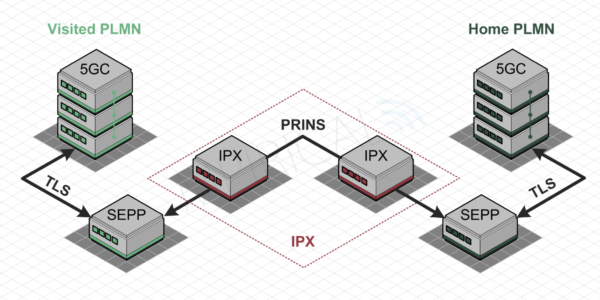 Figure 2 Securing the 5G Control Plane — PRINS
Figure 2 Securing the 5G Control Plane — PRINSTherefore, as an example, let us consider the case of a network function in a visited 5G network wishing to send a message to a network function in a home 5G network i.e. an AMF (Access and Mobility Management Function) requesting authentication parameters from the AUSF (Authentication Server Function). As this is a roaming scenario, the communication will need to pass via N32 and in so doing, utilize both a cSEPP (consumer SEPP) and pSEPP (producer SEPP).
The cSEPP will receive the message from the AMF and applies symmetric key application layer protection i.e. JWE. This is then forwarded to the intermediaries within the IPX which are termed cIPX should they have commercial relationship with the consumer network (VPLMN in our example) and pIPX if the commercial relationship is with the producer network (HPLMN in our example). The cIPX and pIPX entities can therefore offer services to the network which may require modifications to the message being transferred across N32 / IPX. If so, these modifications are then appended to the original message and digitally signed using JWS.
Finally, the pSEPP which receives the message from the pIPX is able to validate the message from the cSEPP using JWE and extract the original message from the AMF. Furthermore, it can also validate any modifications made by either the cIPX or pIPX using JWS, apply the patches corresponding to these modifications before actually forwarding the message to the AUSF. This is illustrated in Figure 3.
Securing the User Plane
In addition to securing the control plane between home and visited networks, it is also necessary to protect the user plane and in particular, the N9 interface linking the UPF (User Plane Function) in the two networks. This interface, like that of S8 in 4G, uses the GTP (GPRS Tunnelling Protocol) to carry user plane traffic between the two networks, typically spanning an IPX. This is illustrated in Figure 4.
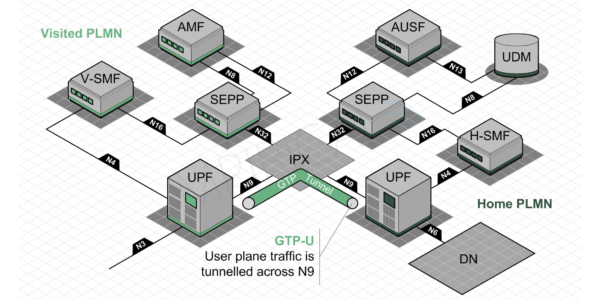
Inter PLMN User Plane Security
To protect this connection, the 3GPP have introduced IPUPS (Inter PLMN User Plane Security) which can either operate on an existing UPFs sitting on the edge of the 5G core network or alternatively can be housed in a specific UPF solely supporting IPUPS.
During the establishment of the PDU (Protocol Data Unit) Session, which in the case of home routing triggers the creation of the GTP tunnel between two UPF. In so doing, a TEID (Tunnel Endpoint Identity) is allocated at each end of the connection and, in association with an IP address at the corresponding UPF, uniquely identifies a specific PDU Session. Therefore, in the case of IPUPS, the two corresponding SMF (Session Management Function), responsible for establishing the PDU Session will also provision both an uplink and downlink PDR (Packet Data Rule) at the UPF such that any traffic either miss formed or not aligned to a valid TEID, will simply be dropped by the UPF in question. In this way, only valid traffic adhering to an active PDU Session will be passed between the visited and home networks.
