
5G New Security Challenges
The development and implementation of 5G has gone hand in hand with discussion surrounding the enhancement of security for mobile networks. This has seen security led collaboration between 3GPP, ETSI, and IEFT standards outlining a new authentication framework, enhanced subscriber privacy, improved core network security, expanded roaming security, and advanced integrity protection of the user plane.
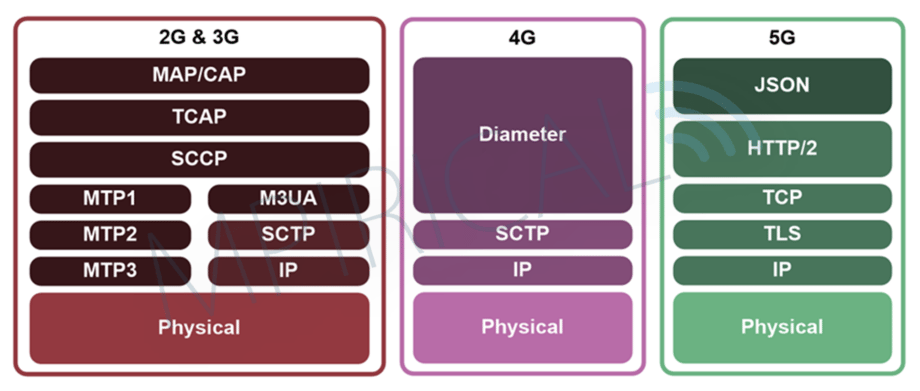
But its implementation has created security concerns. Previous generations of cellular networks rely on the niche SS7 and Diameter protocols. The 5G network core is built on well-known internet protocols such as HTTP and TLS. These changes give some reason for anxiety because the closed nature of telecom protocols acted as a barrier to entry for attackers. In contrast, Internet technologies are open and well known to attackers are there are many tools and approaches to searching for vulnerabilities and they are well documented. 5G aligning with traditional IT infrastructure lowers the entry barrier an creates more potential attack vectors. Attackers who were previously deterred by the complex telecom specific protocols will now have the ability to target 5G networks built on the already popular protocols and technologies.
If you’re interested in exploring additional security challenges faced by 5G, feel free to check out our video on “5G New Security Challenges” which also covers Network Slices, IoT Security, and Cloudification.
